Nmap
Scanning tools are useful both to hackers and system administrators. Nmap is a very useful, free scanning utility. The first objective is to find out what hosts are out on a network. Issuing the command “nmap -sP 192.168.100.*” would bring back all the hosts on the 192.168.100.0 network.

example of using nmap -sP
The next step is to stack fingerprint the network using the command “nmap -sT 192.168.100.102”:

nmap -sT
To see what Nmap is doing, you can use Wireshark to capture the packets that go to and from the target computer. Here’s an example of nmap hitting port 80 on the target computer:

This command (nmap -sT) shows you the ports open on the target system, as well as the services running on those ports. This can help you identify what operating system the computer is running which allow you to probe deeper and find out, for example, the type of server and version. If you’re worried about your scan showing up on the target computer’s logs (as evident in the three-way handshake completed when identifying port 80 as open in the above image), you can do a stealth mode scan with “nmap -sS x.x.x.x”.
Running the command “nmap -O x.x.x.x” will have Nmap guess the operating system on the machine. I didn’t have much success with that command (from the command line), but using the GUI and command “nmap -T4 –version-light -sV -F -O 192.168.100.102”, it guessed the OS as Windows along with a list of possible versions.
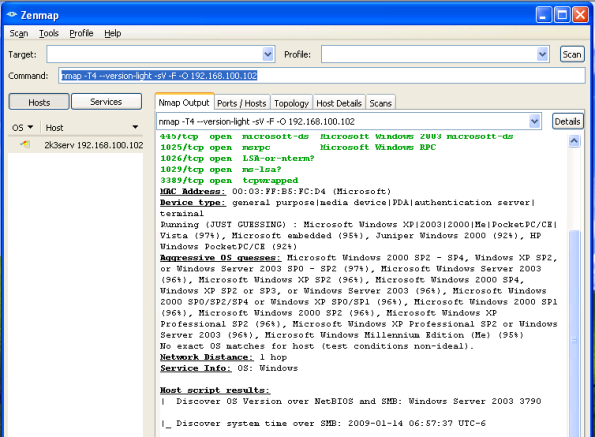
Nmap GUI
Network traffic generated from using Nmap, shown by its signature, can be very detectable. Nmap can be configured to mask its signature from being easily detected.